Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
There is an interesting new pattern by scammers to make compromised wallets completely break so you can't send any funds to it for any rescues. TL;DR: If you EIP-7702 _self-delegate_ your wallet address you completely brick your wallet. So how does this work? If you set your own EOA wallet as delegation address, the code set at your wallet is `0xef0100 || your_address`. Now according to EIP-7702, the delegation indicator uses the _banned_ opcode `0xef` to indicate that the code must be handled differently than regular code. So all good? You might even think this will create a potential infinite chain/loop of delegations, but no, according to the specs: "clients must retrieve only the first code and then stop following the delegation chain." So what happens is that when you self-delegate to your own address, you invoke effectively the invalid opcode `0xef` for every tx going through your wallet and the transaction will revert.
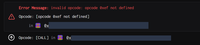
But you can simply solve this, by using my rescue script that can rescue all funds from a compromised wallet using a paymaster and a friendly delegator & there is _no need_ to send ether to the compromised wallet at all.
I mean you can technically force ETH into any account as well, but this approach is so much cleaner to rescue anything from a compromised wallet.
13,46K
Johtavat
Rankkaus
Suosikit













