Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
Earlier this week security tool Socket reported a number of popular NPM packages were compromised, which likely compromised developer machines.
Let's see how this exploit worked and how you can protect yourself against it 👇
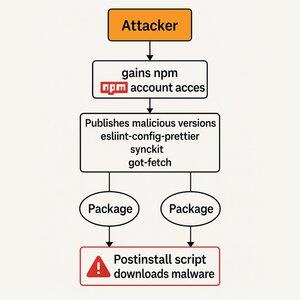
Step 1: NPM publisher access
The hackers used phishing to compromise accounts with publishing rights to these packages.
This allowed the hackers to publish malicious versions of these popular NPM packages.
Step 2: Dependency installation downloads malware
When a developer then installs that new malicious version, a "postinstall" script in the NPM package runs after installation, and downloads + executes malware on the developer machine.
This can compromise further developer accounts or steal credentials from their computer.
How can we stay safe from this kind of exploit?
As a package author:
Employ 2FA so that phishing campaigns are less likely to compromise publishing rights to your packages.
As a developer:
1. Lock down dependencies.
This is luckily already standard practice, or the impact of this exploit would have been much higher.
2. Avoid postinstall scripts where possible.
Most packages do not need a postinstall script to function, so turning them off is recommended. MetaMask has created a great open source tool for this called LavaMoat.
3. Audit dependencies.
The best way to protect against these kinds of exploits is being careful about the dependencies that you add to your project in the first place. Socket is a very useful tool to help with automating that kind of auditing.

320
Johtavat
Rankkaus
Suosikit













